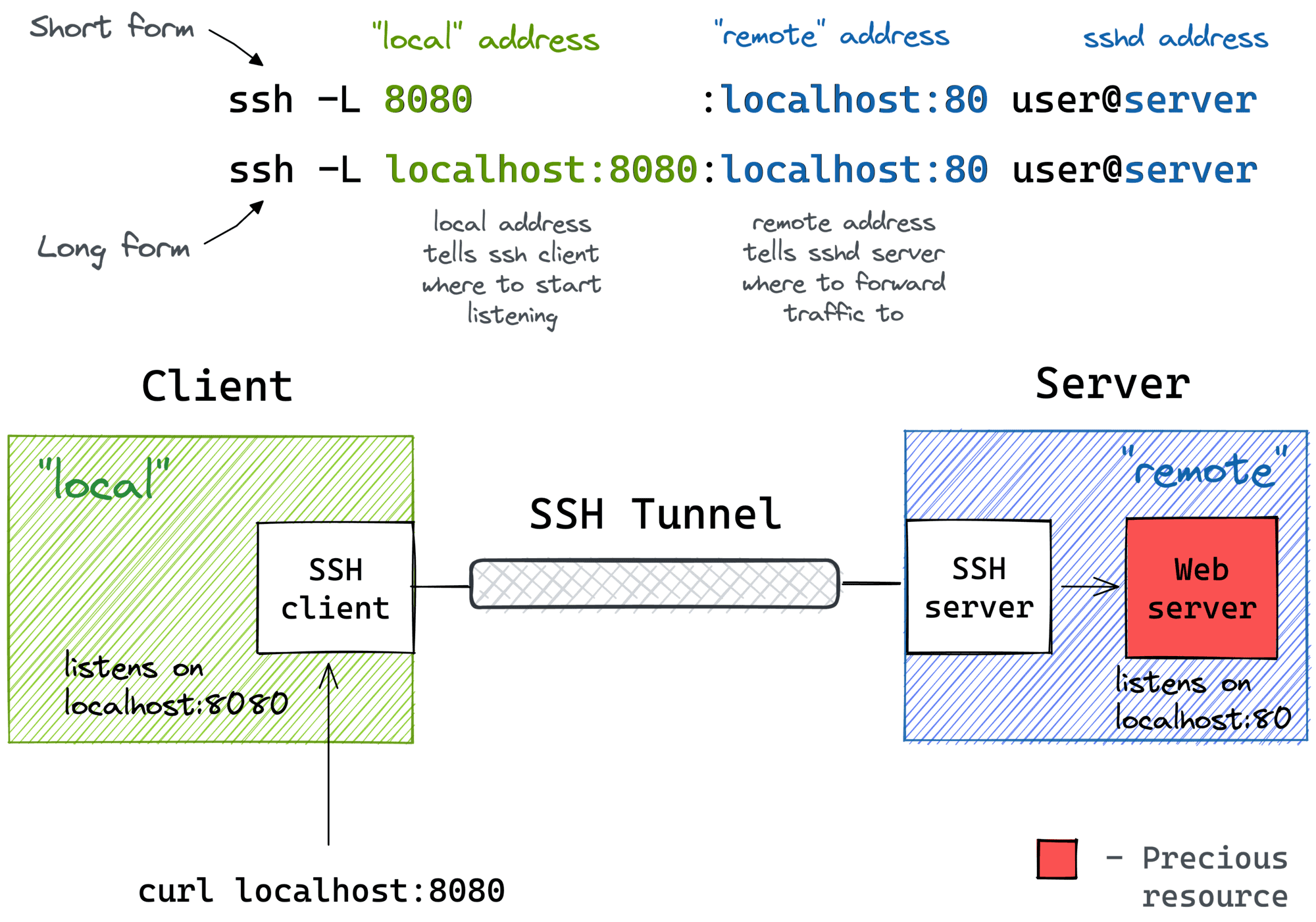
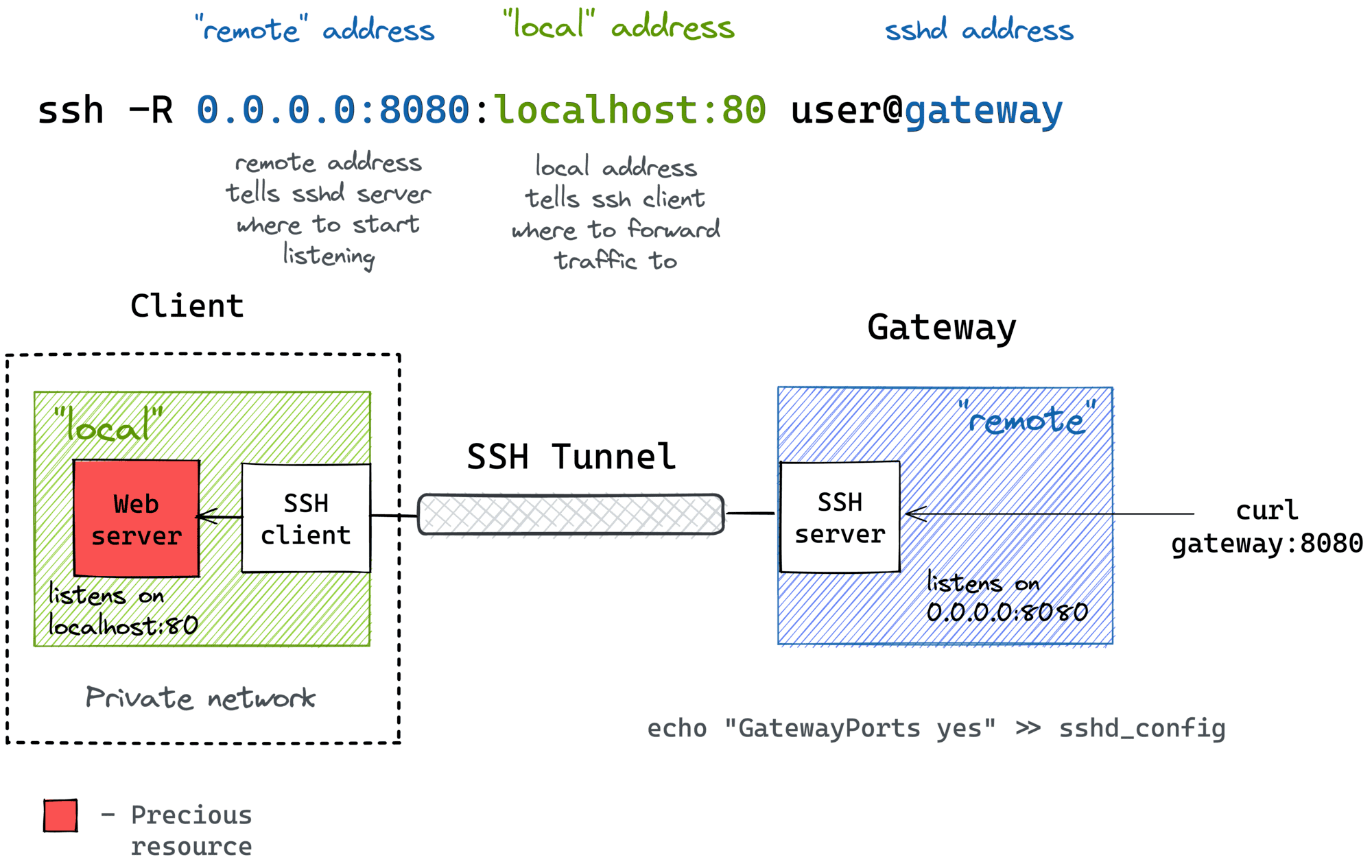
Imagine this: you're working with IoT devices, and you want to ensure secure communication between them. Enter IoT SSH over SSH – a game-changer in the world of secure device management. This technique allows you to create a double layer of security by tunneling SSH connections over another SSH session. If that sounds complicated, don’t worry – we’ve got you covered. In this guide, we’ll break it down step by step so you can master IoT SSH over SSH like a pro.
Nowadays, securing IoT devices has become more critical than ever. Hackers are getting smarter, and vulnerabilities are lurking around every corner. That’s where IoT SSH over SSH comes in handy. By using this method, you can protect sensitive data and ensure that your devices remain safe from unauthorized access.
In this article, we’ll dive deep into the concept of IoT SSH over SSH, provide real-world examples, and offer practical tips to implement it effectively. Whether you’re a beginner or an advanced user, there’s something here for everyone. So, let’s get started!
- Lacykim A Rising Star In The Evolving Digital Landscape
- Unveiling The Dark Side Of Digital Intimacy The Battle Against Unauthorized Content Distribution
What is IoT SSH Over SSH?
IoT SSH over SSH is essentially a security technique that involves tunneling an SSH connection through another SSH connection. Think of it as a double lock on your front door – the more layers of security, the harder it is for intruders to break in. This method is particularly useful when dealing with IoT devices that need to communicate securely over untrusted networks.
SSH, or Secure Shell, is a cryptographic protocol used to secure communication between devices. When you add another layer of SSH on top of it, you’re essentially creating a secure tunnel within a secure tunnel. This makes it nearly impossible for hackers to intercept or tamper with your data.
For example, imagine you’re managing a smart home system with multiple IoT devices. By using IoT SSH over SSH, you can ensure that all communication between these devices remains encrypted and secure, even if someone tries to eavesdrop on the network.
- Unraveling The Dark Side Of Movierulz A Deep Dive Into The World Of Film Piracy
- Emerging Technologies The Catalyst For Digital Transformation
Why Use IoT SSH Over SSH?
Security is the name of the game here. IoT devices are often deployed in environments where network security is not guaranteed. Whether it’s a public Wi-Fi network or a corporate LAN, there’s always a risk of unauthorized access. IoT SSH over SSH helps mitigate these risks by adding an extra layer of protection.
Here are some key benefits:
- Enhanced security through double encryption
- Protection against man-in-the-middle attacks
- Easy to implement with minimal overhead
- Compatibility with most modern devices and operating systems
In today’s interconnected world, where data breaches and cyberattacks are becoming more common, it’s crucial to adopt robust security measures. IoT SSH over SSH is one such measure that can significantly enhance the security of your IoT infrastructure.
How Does IoT SSH Over SSH Work?
Let’s break it down step by step. First, you establish an SSH connection from your local machine to a remote server. This is your primary SSH tunnel. Then, you create another SSH connection within this tunnel, connecting to the target IoT device. This secondary connection is encrypted and secured by the primary SSH tunnel, ensuring that all data transmitted between your machine and the IoT device remains safe.
Here’s a simplified example:
- Step 1: Connect to the remote server using SSH.
- Step 2: From the remote server, connect to the IoT device using another SSH session.
- Step 3: All communication between your local machine and the IoT device is now encrypted twice – once by the primary SSH tunnel and once by the secondary SSH connection.
This process might sound complex, but with the right tools and configurations, it can be implemented fairly easily. Plus, most modern SSH clients support this functionality out of the box.
Setting Up IoT SSH Over SSH
Now that you understand the concept, let’s talk about how to set it up. First, you’ll need an SSH client on your local machine. Popular options include OpenSSH for Linux and macOS, and PuTTY for Windows. Next, you’ll need access to a remote server that can act as the intermediary between your local machine and the IoT device.
Step-by-Step Guide
Here’s a step-by-step guide to setting up IoT SSH over SSH:
- Install an SSH client on your local machine.
- Obtain the IP address or hostname of the remote server.
- Establish an SSH connection to the remote server using the command:
ssh user@remote_server. - Once connected to the remote server, establish another SSH connection to the IoT device using the command:
ssh user@iot_device. - Verify that both connections are active and functioning properly.
That’s it! You now have a secure IoT SSH over SSH setup that can protect your devices from potential threats.
Best Practices for IoT SSH Over SSH
To get the most out of IoT SSH over SSH, it’s important to follow some best practices. Here are a few tips to keep in mind:
- Always use strong, unique passwords for your SSH connections.
- Enable two-factor authentication (2FA) wherever possible.
- Regularly update your SSH clients and servers to ensure they’re running the latest security patches.
- Limit access to your SSH ports by configuring firewalls and access controls.
- Monitor your SSH logs for any suspicious activity.
By following these best practices, you can further enhance the security of your IoT SSH over SSH setup and protect your devices from potential threats.
Common Use Cases for IoT SSH Over SSH
IoT SSH over SSH is versatile and can be applied to a variety of use cases. Here are some common scenarios where this technique is particularly useful:
- Remote management of IoT devices in untrusted networks.
- Secure communication between IoT devices in industrial settings.
- Protecting sensitive data transmitted between IoT devices and cloud servers.
- Ensuring secure access to IoT devices for maintenance and troubleshooting.
Whether you’re managing a smart home system or overseeing an entire IoT infrastructure, IoT SSH over SSH can help you maintain secure and reliable connections.
Real-World Examples of IoT SSH Over SSH
Let’s look at a few real-world examples to see how IoT SSH over SSH is being used in practice:
Example 1: Smart Home Security
In a smart home setup, IoT SSH over SSH can be used to secure communication between smart locks, cameras, and other devices. By tunneling SSH connections through a remote server, homeowners can ensure that their devices remain safe from unauthorized access, even when connected to public Wi-Fi networks.
Example 2: Industrial IoT
In industrial settings, IoT SSH over SSH is often used to secure communication between sensors, actuators, and control systems. This ensures that critical data remains protected and that operations continue smoothly without interruptions.
Example 3: Cloud-Based IoT Solutions
Many cloud-based IoT solutions rely on IoT SSH over SSH to secure communication between edge devices and cloud servers. This allows organizations to manage their IoT infrastructure remotely while maintaining high levels of security.
Challenges and Limitations of IoT SSH Over SSH
While IoT SSH over SSH offers numerous benefits, it’s not without its challenges. Here are some potential limitations to consider:
- Increased latency due to double encryption.
- Higher resource consumption on both the local machine and the remote server.
- Complexity in setup and configuration for beginners.
Despite these challenges, the added security provided by IoT SSH over SSH often outweighs the drawbacks, especially in high-risk environments.
Future Trends in IoT SSH Over SSH
As IoT technology continues to evolve, so too will the methods used to secure it. Future trends in IoT SSH over SSH may include:
- Integration with blockchain technology for enhanced security.
- Use of quantum cryptography for unbreakable encryption.
- Development of more user-friendly tools and interfaces for easier setup and management.
By staying ahead of these trends, you can ensure that your IoT infrastructure remains secure and future-proof.
Conclusion
In conclusion, IoT SSH over SSH is a powerful tool for securing IoT devices and ensuring safe communication between them. By adding an extra layer of encryption, you can protect your devices from potential threats and maintain the integrity of your data.
We’ve covered everything from the basics of IoT SSH over SSH to real-world examples and future trends. Now it’s your turn to put this knowledge into practice. Whether you’re managing a smart home system or overseeing an industrial IoT infrastructure, IoT SSH over SSH can help you achieve the level of security your devices need.
So, what are you waiting for? Start securing your IoT devices today and take the first step towards a safer, more connected world. Don’t forget to share your thoughts and experiences in the comments below, and be sure to check out our other articles for more tips and tricks on IoT security.
Table of Contents
- What is IoT SSH Over SSH?
- Why Use IoT SSH Over SSH?
- How Does IoT SSH Over SSH Work?
- Setting Up IoT SSH Over SSH
- Best Practices for IoT SSH Over SSH
- Common Use Cases for IoT SSH Over SSH
- Real-World Examples of IoT SSH Over SSH
- Challenges and Limitations of IoT SSH Over SSH
- Future Trends in IoT SSH Over SSH
- Conclusion
- Unveiling The Dark Side Of Online Fame Isla Mylarsquos Story And Its Broader Implications
- Robert Lopez Steering The Future Of Technology At Ces 2025